System Architecture
1) High‑Level Design
IntelliHome separates the control plane (Ryu apps + policy/analytics) from the data plane (Open vSwitches in Mininet). Packets traverse programmable switches, followed by decisions (allow/blocked/malicious/benign) made centrally using MUD policy checks, ML inference, and a PageRank‑style trust score.
- Data Plane: Mininet virtual switches (OpenFlow 1.3), IoT hosts, Internet gateway.
- Control Plane: Ryu controller with modular apps:
- Topology & Flow Monitor
- MUD Policy Engine
- ML Inference Engine
- Trust Scoring (PageRank)
- REST API (Northbound) for UI
- Presentation Layer: This website (status, logs, charts, demo).
System Diagram
The following diagram illustrates the core components and data flow within IntelliHome SDN:
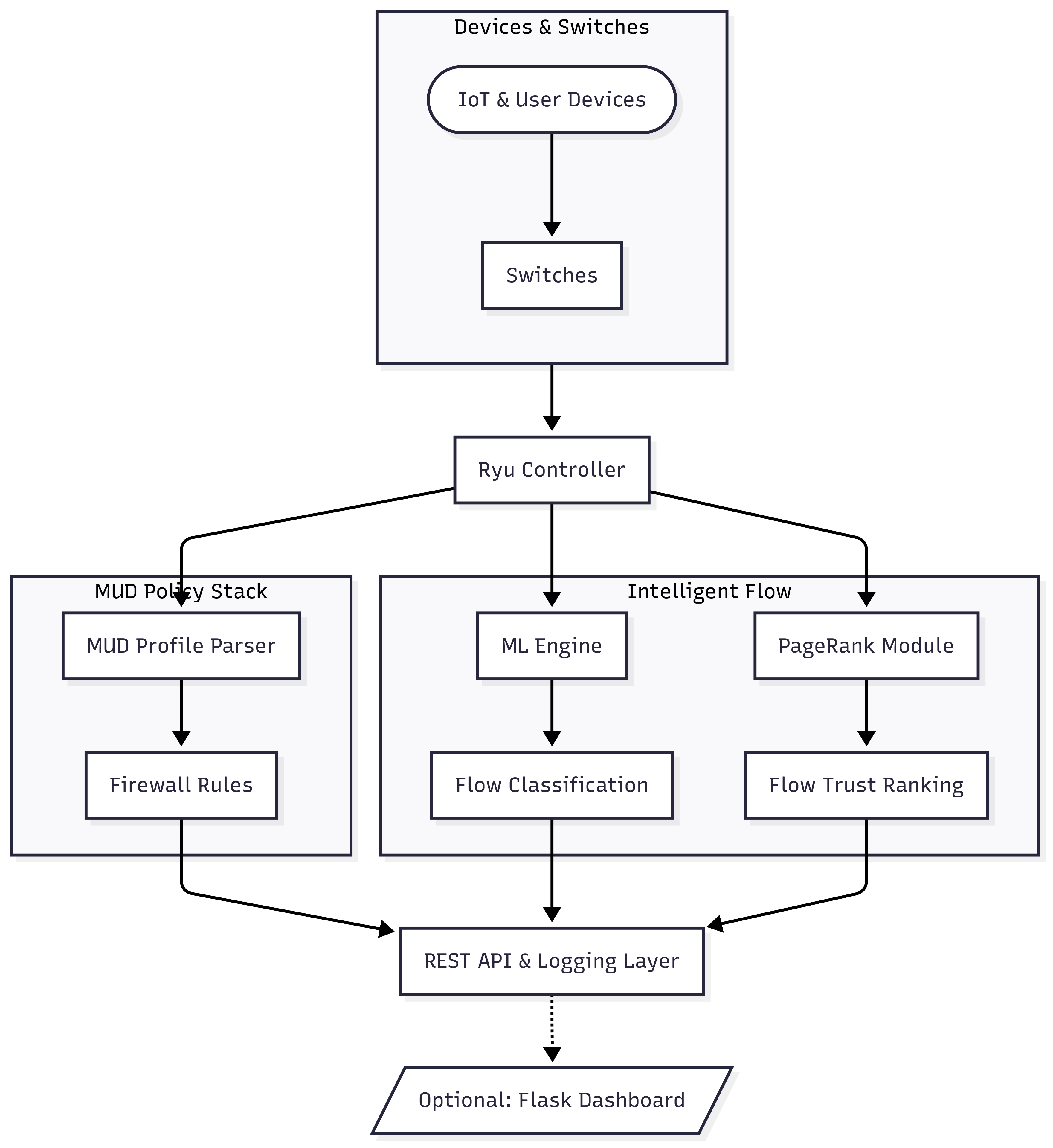
Module Map (This Project)
- Ryu App:
ryu_project.py— main OpenFlow 1.3 controller (SimpleSwitchRouting), REST (MudRestController). - MUD Policy Data:
mud_policy— device allowlists (see “MUD Policy Engine”). - ML Inference:
model_engine.py—classify_flow(features), loadsrf_model.pklvia joblib/pandas.
The Ryu app in ryu_project.py drives the control plane. Switches (OVS) form the data plane in Mininet.
For each new flow: MUD baseline check → ML inference via model_engine.classify_flow → Trust (PageRank) → fused decision → OpenFlow rules.
2) Components & Responsibilities
- Ryu App (
ryu_project.py)SimpleSwitchRouting— OpenFlow 1.3, topology/mac tables, flow installs, flood detection.MudRestController— REST endpoints for UI.
- MUD Policy Engine (data-driven) — loads allowlists from
mud_policy(see note below) and enforces device-specific baselines. - ML Inference (
model_engine.py) —classify_flow()returns"benign"/"malicious"usingrf_model.pkl. - Trust Scoring — NetworkX PageRank (in
ryu_project.py) on host-to-host edges; recompute periodically. - Northbound REST — JSON for blocked flows and trust scores (see §6).
3) Data & Control Flow
- PacketIn → Ryu.
- MUD pre-check. If src⇢dst violates the device baseline from
mud_policy, mark and block/quarantine. - Feature extraction. proto, pkt_len, src_port, dst_port (passed to ML).
- ML inference.
from model_engine import classify_flow→classify_flow(features). - Trust update. Add edge src→dst to
trust_graph, recompute PageRank periodically. - Decision. Fuse MUD ∧ ML ∧ Trust → allow / rate-limit / quarantine / block.
- Program switch. Issue
flow_modwith timeouts & priority. - Expose state. Append to logs & expose via REST for UI.
4) OpenFlow Pipeline (Tables)
- Table 0 — Classify: match L2/L3/L4; set metadata (device_id);
GOTO:10. - Table 10 — Policy: MUD allow/deny & optional meters;
GOTO:20. - Table 20 — Forward: output or controller on miss.
# conceptual rules installed by ryu_project.py
table=0 match:ip_proto=6,tp_dst=443 actions:set_field:device=cam1,GOTO:10
table=10 match:device=cam1,policy=allow_tls actions:meter:1,GOTO:20
table=10 match:device=cam1,ip_proto=17,tp_dst=23 actions:drop
table=20 match:nw_dst=10.0.0.42 actions:output:3
5) Decision Logic (Fusion)
- MUD:
ALLOW/DENY/UNKNOWNfrommud_policy. - ML:
classify_flow()→"benign"/"malicious". - Trust: normalized PageRank score ∈ [0,1].
// in ryu_project.py (conceptual)
if MUD == "DENY":
action = DROP
elif ML == "malicious":
action = QUARANTINE if Trust < 0.2 else DROP
elif MUD == "ALLOW" and ML == "benign" and Trust > 0.4:
action = ALLOW
else:
action = RATE_LIMIT
6) Northbound REST API (from MudRestController)
GET /mud/blocked→ list of blocked/quarantined flows.GET /api/trust→ current PageRank trust scores.
{
"device": "thermostat-1",
"flow": "10.0.0.5:443/tcp → 8.8.8.8",
"mud": "ALLOW",
"ml": "benign",
"trust": 0.63,
"decision": "ALLOW",
"switch": "s1", "table": 20, "priority": 200, "idle_timeout": 60
}
7) MUD Policy Engine
- Source:
mud_policyfile with per-device allowlists (IP/ports/directions). - Load in
ryu_project.py: parse to internal templates; proactively install allow rules; default-deny everything else. - Drift: traffic outside baseline → extra scrutiny (ML + Trust) and potential quarantine.
8) ML Inference (model_engine.py)
- Model file:
rf_model.pkl(joblib). - Signature:
classify_flow({"proto","pkt_len","src_port","dst_port"}) → "benign"|"malicious"|"unknown". - Integration in
ryu_project.py:from model_engine import classify_flow; call only after MUD allows.
9) Trust Scoring (PageRank in ryu_project.py)
Maintain trust_graph (directed src→dst edges on allowed flows). Recompute trust with networkx.pagerank() periodically
(e.g., every 20 new edges) and expose via /api/trust.
10) Telemetry, Logging & Storage
- Blocked flows: append to
self.blocked_flows(served by/mud/blocked). - Counters: per-device flow verdicts, flood-detect hits, rule install counts, latency.
- Export: optional CSV/JSON for the Results page.
11) Security & Failure Considerations
- Fail-safe: if ML or MUD data unavailable → default to strict allowlist + rate-limit + alert.
- REST hardening: validate inputs; restrict methods; audit overrides.
- Timeouts: use
idle_timeoutto clear stale reactive rules.
12) Performance & Scalability
- Proactive MUD rules reduce PacketIn load.
- Batch PageRank recomputation (edge threshold) and ML gating (after MUD) prevent hot paths.
- Meters/groups can rate-limit suspected flows.
13) Configuration (Excerpt)
{
"openflow": "1.3",
"timeouts": { "idle": 60, "hard": 0 },
"flood": { "PACKET_THRESHOLD": 1000, "TIME_WINDOW_SEC": 200 },
"ml": { "module": "model_engine.py", "model_file": "rf_model.pkl" },
"trust": { "recompute_every_edges": 20, "alpha": 0.85 },
"mud": { "file": "mud_policy.json", "default_policy": "deny" }
}
14) Demo Runbook
- Start controller:
ryu-manager ryu_project.py --observe-links - Launch Mininet:
sudo mn --custom topo.py --topo intellihome --controller=remote,ip=127.0.0.1,port=6633 --switch ovs,protocols=OpenFlow13 - Generate benign + attack traffic; watch Demo & Results pages pull from
/mud/blockedand/api/trust.
